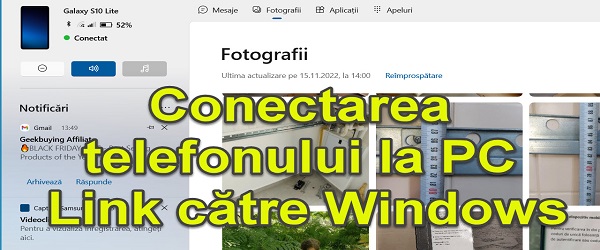
The perfect connection between Windows and Android What is the video tutorial about The perfect connection between Windows and Android This tutorial will show you how to make the perfect connection between Windows and Android. We will use on Windows the application called Link to the phone, and on Android we will use the application Link to Windows; The last one, on the phones... [Read more...]
The seamless connection between Windows and Android Link to phone - reissue
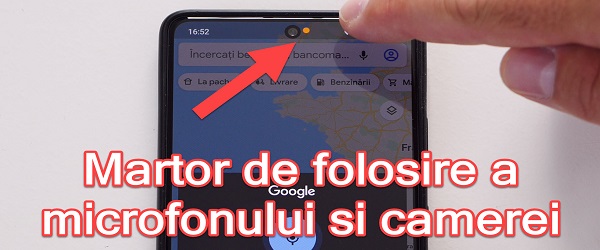
How to turn off the Android microphone and camera - TURN OFF SENSORS
What is the video tutorial about turning off your Android microphone and camera? In this tutorial you will see How to turn off the microphone and the Android camera. It is an emergency measure that you take when you suspect that there is spy software on your phone. In addition to blocking spyware access to the camera, microphone, or other sensors, this method of stopping… [Read more...]
AnyDesk best remote software - better than TeamViewer
AnyDesk best remote software What is this AnyDesk best remote software tutorial about? In the AnyDesk best remote software video tutorial, I present the best remote software, easy to use for everyone. Of course there are a lot of remote softwares that offer even more, but AnyDesk is very easy to use even by those with [Read more...]
Correct setting of TeamViewer QuickSuport on your phone - connection problems
Correctly setting TeamViewer QuickSuport on your phone What is the tutorial about Setting up TeamViewer QuickSuport on your phone correctly? In the video tutorial Correct setting TeamViewer QuickSuport on your phone I show you how to make settings for TeamViewer and TeamViewer QuickSuport applications in the android system. Specifically, you'll see the settings that make these apps… [Read more...]
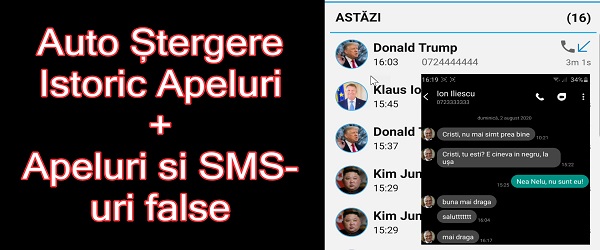
Auto delete history call certain contacts and SMS and fake calls
What is the video tutorial about deleting certain contacts call history? In the tutorial I present an application that with 3 functions: auto delete history call certain contacts, and planting fake sms and fake calls. What is the name of the application for auto deleting call history of certain contacts? The application is called Call Log Monitor and is not found by… [Read more...]
Detector fraudulent use of microphone and camera on Android phones
What is the Fraud Microphone and Camera Use Detector tutorial about? In this video tutorial I present a detector for fraudulent use of microphone and camera, ie an application that detects and notes when the camera and microphone are used on Android phones. Why would we want to know when the camera and microphone on the phone are used… [Read more...]
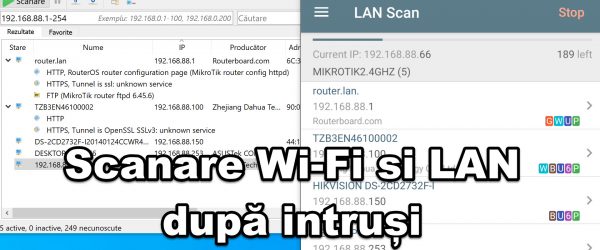
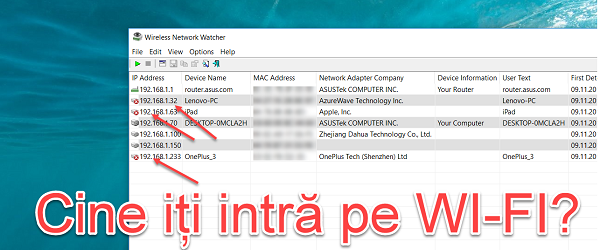
Who's connected to your network? - see everything connected to the network
Who is connected to your network? In this video tutorial you will see how we can find out who is connected with the devices to our network, we will also find out the devices that are connected to the network. Find out who steals your Wi-Fi network who is connected to your network When is it useful to find out which devices are connected to our network? When you forgot your IP [Read more...]
Spy microphone detector GPS trackers and tracking devices
GPS spy tracker microphone detector What is a GPS tracker spy microphone detector for? If you are an important person or simply have a paranoid life partner, you may be tracked by a spy microphone or GPS tracker, and that's why you need a spy microphone detector and GPS trackers. On what principle does it work… [Read more...]
Who connects illegally on your WI-FI network
Who connects illegally on your WI-FI network The wireless signal passes through the walls of the house. When we use a Wi-Fi network in our home, we need to be aware that that wireless network can also be accessed by other people, neighbors, or people nearby. Better security of the Wi-Fi network We have spoken on other occasions about security when logging in… [Read more...]










Recent Comments