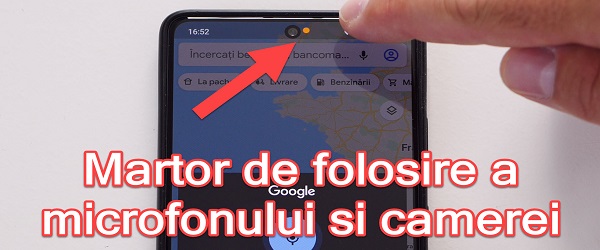
What is the Fraud Microphone and Camera Use Detector tutorial about? In this video tutorial I present a detector for fraudulent use of microphone and camera, ie an application that detects and notes when the camera and microphone are used on Android phones. Why would we want to know when the camera and microphone on the phone are used… [Read more...]
Detector fraudulent use of microphone and camera on Android phones
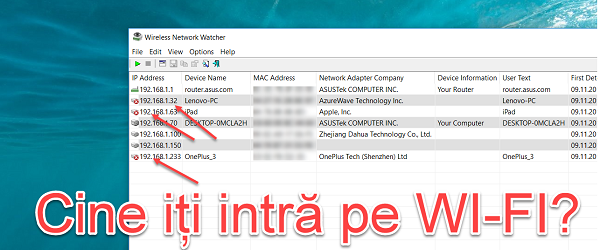
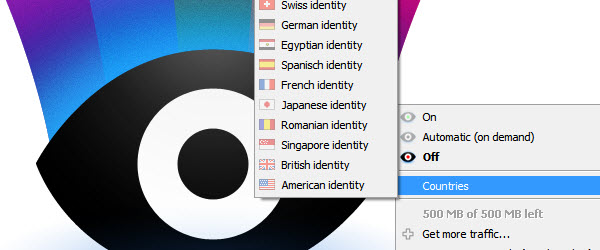
Who connects illegally on your WI-FI network
Who connects illegally on your WI-FI network The wireless signal passes through the walls of the house. When we use a Wi-Fi network in our home, we need to be aware that that wireless network can also be accessed by other people, neighbors, or people nearby. Better security of the Wi-Fi network We have spoken on other occasions about security when logging in… [Read more...]
KRACK affects ALL Wi-Fi routers - SOLUTIONS
KRACK affects ALL Wi-Fi routers - SOLUTIONS Krack threatens all Wi-Fi routers. What solutions do we have? What is KRACK ATTACK? KRACK is a vulnerability discovered in the WPA2 protocol, to which all routers in the world are vulnerable. How does KRACK work? The attacker who exploits the KRACK vulnerability, interposes himself between the router and the client (phone,… [Read more...]
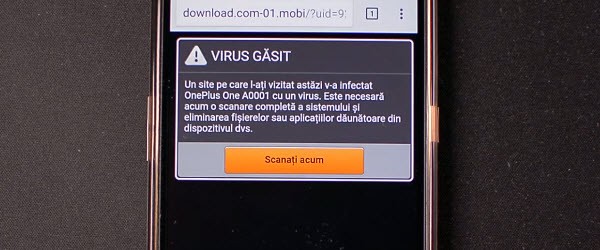
How to get rid of scareware phone
Scareware programs or pages are a special and very passive category of malware. They are a kind of phishing that is based on users' fears to determine them to perform certain actions. A scareware can urge you to install software, disclose personal data, pay a certain amount of money or send an SMS to a number with [Read more...]
ANTI-HACK, Redirect vulnerability to SMB
Hello friends, today we will solve the problem with the "Redirect to SMB" vulnerability that was discovered a few days ago and that affects all versions of Windows, including Windows 10. The vulnerability is based on the naivety of Windows applications that want to log in as soon as they feel an SMB server. At that moment the login data is spit out, where the attacker… [Read more...]
Freedom Okay, pay online and browsing safely
Hello friends, in today's tutorial I will present a free and very fast VPN service. The VPN service is called Okay Freedom and is offered free of charge by Steganos, known for its slightly more secular security software products. Some time ago in the tutorial "Wireshark, intercepting passwords on free wi-fi networks" I showed you how easy it is. It is … [Read more...]
Simple measures to secure and encrypt traffic navigation
Hi friends, in today's tutorial we will see some tips for safer browsing and encrypted traffic when using a public wireless network. If in yesterday's tutorial about Wireshark, intercepting passwords on free wi-fi networks, my colleague Cristi will show you how easy it is for someone to intercept the data we enter into a site, today [Read more...]
DNS poisoning method commonly used by hackers
DNS poisoning is a method by which hackers give the impression that they have taken control of certain known or unknown sites. DNS is the protocol that makes the link between the domain name and the IP address, because any site in this world has one. or more IP addresses. When we type in the browser "google.com" our computer has three options for finding the address… [Read more...]
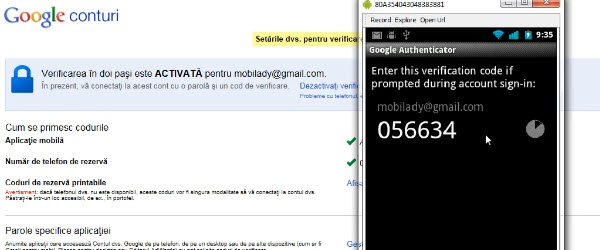
Keep hackers at bay with two-step verification for your Google Account - video tutorial
Hi friends, in today's tutorial we will see how we can secure your Google account so that it can be impossible to break. Specifically, we will talk about the "2-step verification" or "XNUMX step verification" option offered by Google for its users in order to protect your account very well. As the name suggests, this option adds a second step that [Read more...]








Recent Comments