Hello friends, in today's tutorial we will talk about securing your Facebook account. Specifically, we will see how we can set up our Facebook account so that it is impossible to access even by those who know our email and Facebook account password. We decided to make this tutorial because many acquaintances and friends of the site -they said their password was broken… [Read more...]
How to find out if and when someone uses our Yahoo account and Yahoo Messenger ID - video tutorial
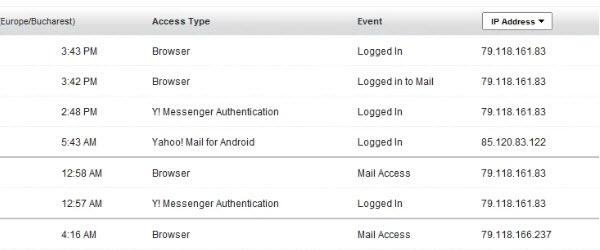
Hi friends, in today's tutorial we will see how we can find out if someone uses our Yahoo account. As I told you in the tutorial on How to find out if and when someone uses our Facebook account, most online services offer this type of logs. Yahoo is no exception to this feature and offers its users the opportunity to find out: time and date, [Read more...]
CurrPorts helps us monitor the network and find out the ip of those we chat with - video tutorial
Hello friends, in today's video tutorial I will introduce you to an application for monitoring the network and especially the software that uses the internet connection, the application is called CurrPorts and is extremely friendly, even with inexperienced users. Plenty of programs like this, CurrPorts has more advantages compared to… [Read more...]
Predator, software that together with a USB stick can quickly lock and unlock the computer - video tutorial
Hi friends, in this video tutorial I will introduce you to an interesting program, it is called Predator and it can help us turn a usb stick into a computer key, from now on we can lock and unlock your pc almost instantly without inserting it in standby or hibernation. Predator uses the usb stick to store a "key" file, this file is read at… [Read more...]
KeyFreeze, software that allows you to lock the keyboard and mouse for security - video tutorial
In today's tutorial I will present a very small software that in some situations is useful. The program is called Key Freeze and with its help we can completely block our mouse and keyboard, ie we can no longer use the computer. How would this program help us? If you are visited by someone and you urgently need to leave computer is [Read more...]
Threat Fire, more than an antivirus, a smart security solution - video tutorial
Hi friends, in today's tutorial we will talk about a free security software, it is revolutionary in many ways, our "smart" today is called Treath Fire and is produced by the well-known company PC Tools.Threat Fire is a security solution smart antivirus type, it is not like a regular antivirus, it can not replace the antivirus, it only comes in… [Read more...]
Kaspersky Internet Security 2010, probably the best security solution - video tutorial
Hello friends, I am pleased to present you with probably the most complete security suite on the market at the moment, it is Kaspersky Internet Security 2010, a much improved and refined suite compared to the previous version (kis 2009). In this video tutorial we will deal in detail with the Kaspersky Internet Security 2010 suite or KIS version 9.0.0.463, this version… [Read more...]






Recent Comments