Hello friends, in today's tutorial we will see how to record a phone call on phones running the Android operating system. From the beginning I want to tell you that in order to put into practice what was shown in this tutorial it is necessary that your phone be rooted (to have root). About what root means or how to root a smartphone, we have more… [Read more...]
Simple measures to secure and encrypt traffic navigation
Hi friends, in today's tutorial we will see some tips for safer browsing and encrypted traffic when using a public wireless network. If in yesterday's tutorial about Wireshark, intercepting passwords on free wi-fi networks, my colleague Cristi will show you how easy it is for someone to intercept the data we enter into a site, today [Read more...]
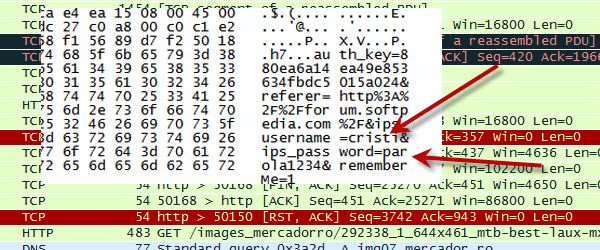
Wireshark, stealing passwords on free wi-fi networks
Today we will do something more special, we will try to intercept the login data from the browser with the help of an extraordinary software called Wireshark. I will show you how easy you can lose your password and username if you use them when you are connected on networks. public networks. These networks are the favorite target of attackers, they capture all traffic… [Read more...]
DNS poisoning method commonly used by hackers
DNS poisoning is a method by which hackers give the impression that they have taken control of certain known or unknown sites. DNS is the protocol that makes the link between the domain name and the IP address, because any site in this world has one. or more IP addresses. When we type in the browser "google.com" our computer has three options for finding the address… [Read more...]
Prey, monitor and find stolen or lost laptop or phone - video tutorial
Hi friends, in today's tutorial we will talk about a software that will help us recover lost or stolen devices whether it is Android tablet, Android smartphone, iPhone with iOS, iPad, Netbook or Notebook running Windows or Linux, products Apple running the Mac OS operating system This is about Prey, an open source project that offers us software… [Read more...]
Setting up a surveillance system, part 2, audio video recording and management - video tutorial
Hello friends, today I will continue with the second part of the series dedicated to video surveillance, in the first tutorial we discussed about installing an IP camera and today we will talk about managing and recording the video signal emitted by the IP camera. If you do not have an IP camera, you can turn your phone into a surveillance camera, or you can turn your webcam and computer… [Read more...]
CurrPorts helps us monitor the network and find out the ip of those we chat with - video tutorial
Hello friends, in today's video tutorial I will introduce you to an application for monitoring the network and especially the software that uses the internet connection, the application is called CurrPorts and is extremely friendly, even with inexperienced users. Plenty of programs like this, CurrPorts has more advantages compared to… [Read more...]
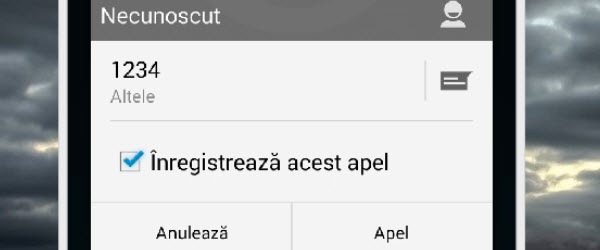
How to find out the phone number of the person who calls us with a hidden number - video tutorial
Hello friends, in today's tutorial we will see how we can find out who is calling us with a hidden number. I think there is no person who has not faced such a dilemma. Most people have suffered at least once in their life to be called or beep-forgotten in the middle of the night by unknown numbers and those who call with a hidden number, often do not know the limits and become… [Read more...]
How to locate and recover a stolen or lost Android mobile phone - video tutorial
Hello friends, in today's tutorial we will learn how we can locate and recover our Android smartphone when we lose it or it is stolen. Because a smartphone generally has a wireless antenna and a GPS module, application developers and security companies have thought of using them to help the customer find their smartphone in [Read more...]
Security in the browser, how we can see the characters of the passwords under the stars - video tutorial
Hi friends, in today's tutorial we will talk about security, browsers, passwords and how we can see the password under the stars in the password fields when we log on to sites. When is it useful for us to be able to see the characters under the stars entered in the password / password field? [Read more...]







Recent Comments