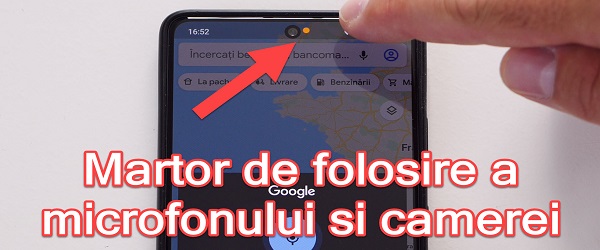
What is the video tutorial about turning off your Android microphone and camera? In this tutorial you will see How to turn off the microphone and the Android camera. It is an emergency measure that you take when you suspect that there is spy software on your phone. In addition to blocking spyware access to the camera, microphone, or other sensors, this method of stopping… [Read more...]
How to turn off the Android microphone and camera - TURN OFF SENSORS
Detector fraudulent use of microphone and camera on Android phones
What is the Fraud Microphone and Camera Use Detector tutorial about? In this video tutorial I present a detector for fraudulent use of microphone and camera, ie an application that detects and notes when the camera and microphone are used on Android phones. Why would we want to know when the camera and microphone on the phone are used… [Read more...]
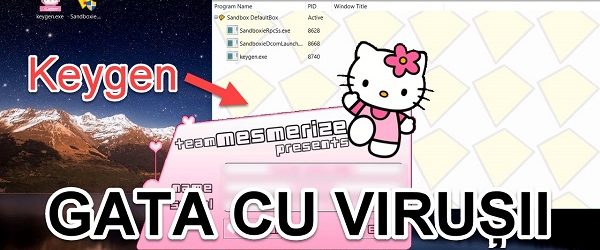
How not to infect infected sites and viruses - sandboxie
How not to get infected on infected sites and virus applications - sandboxie How not to get infected on infected sites and virus applications - sandboxie In recent years people are increasingly dealing with viruses, spyware and other malicious programs of a new type that have become increasingly sophisticated, and which can be difficult to intercept by a… [Read more...]
How to block the misuse of BITCOIN on your PC
How to block abusive BITCOIN mining on PC What about abusive BITCOIN MINING? Lately, due to the ever-increasing price of BITCOIN, hackers are looking for more and more interesting methods of mining BITCOIN. The last method consists in using the processing power of several computers, through software or web scripts, which transform… [Read more...]
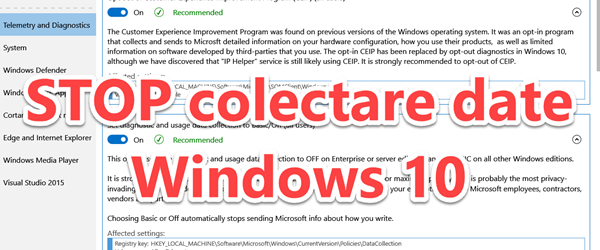
STOP invasion of privacy on the Microsoft WINDOWS 10
STOP Microsoft's breach of privacy on WINDOWS 10 What is the tutorial about? In this tutorial I will show you how you can disable all settings that violate your privacy on Windows 10 by Microsoft, by massively collecting usage data, browsing, preferences, location, etc. STOP the violation of privacy on WINDOWS 10 by… [Read more...]
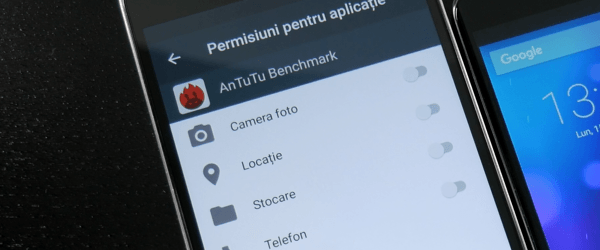
Android permissions 6 Marshmallow
With the launch of Android 6 Marshmallow, this mobile operating system has received granular settings for application permissions; feature that was long awaited on Android; as it was already on iOS. With the new settings, we can control in detail how far the "tentacles" applications can stretch. Most of the time, applications ask for permission in vain, not being… [Read more...]
DNS poisoning method commonly used by hackers
DNS poisoning is a method by which hackers give the impression that they have taken control of certain known or unknown sites. DNS is the protocol that makes the link between the domain name and the IP address, because any site in this world has one. or more IP addresses. When we type in the browser "google.com" our computer has three options for finding the address… [Read more...]
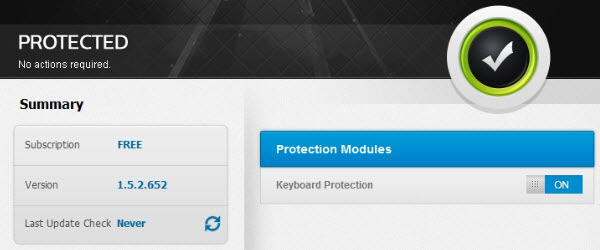
Zemana AntiLogger or how to protect ourselves against data theft and espionage software - video tutorial
Hello friends, in today's tutorial we will talk about the measures we can take against data theft. The most dangerous infections are Keylogger, software that can record what we type on the keyboard. Keyloggers can range from the simplest, easily traceable to the most complex, very difficult to identify. They can also exist in… [Read more...]
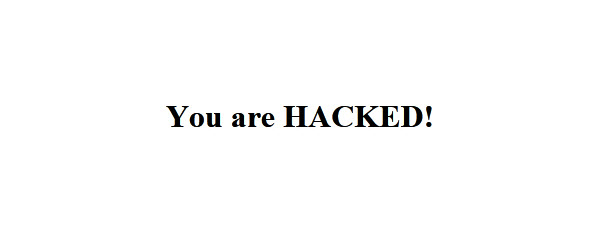
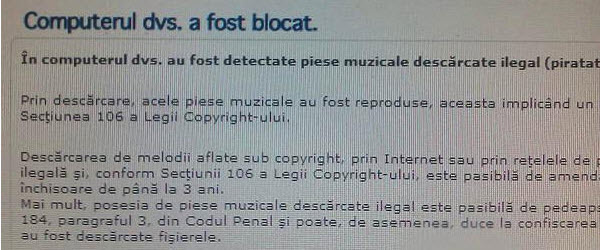
Eliminate ransomware infections with MalwareBytes - video tutorial
Hi friends, in today's tutorial we will talk about Malwarebytes in the conditions in which we became infected with a ransomware. More recently, a new type of infection is circulating on the Internet, which blocks the user's navigation by redirecting him to a site where a message "Your computer has been blocked" is displayed, informing him that he has illegally downloaded content… [Read more...]
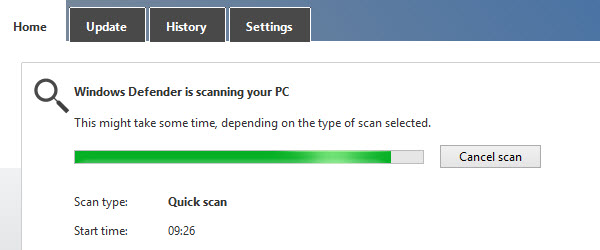
Premiere for Microsoft, Windows 8 comes with preinstalled antivirus - video tutorial
Hi friends, in this video tutorial we will talk about the antivirus that comes preinstalled on Windows 8, yes you heard right, for the first time Microsoft puts an antivirus in the Windows operating system. The antivirus in Windows 8 is called Defender and all you will It seemed familiar, I assure you it's not the old Defender, which was actually an antispyware. ... [Read more...]








Recent Comments