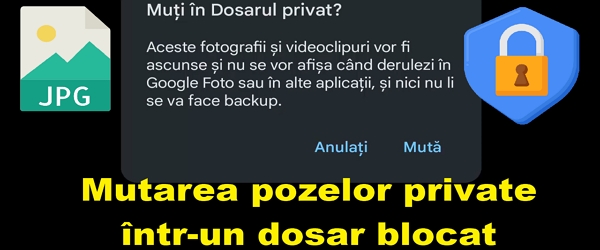
Hide private pictures in a locked folder What is the tutorial Hide private pictures in a locked folder about? In this video tutorial titled Hide private pictures in a locked folder , I show you a method by which you can move private pictures from the gallery to a locked folder that you can only open with your fingerprint This method of … [Read more...]
Hide private pictures in a locked folder – separate from the gallery
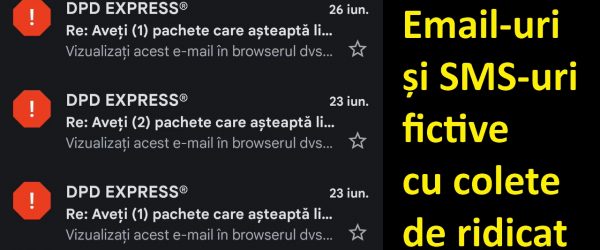
Fraudulent messages with unaddressed parcels – how we tell
What is the video tutorial Fraudulent messages with unaddressed parcels about In this video tutorial Fraudulent messages with unaddressed parcels we will see how we can tell if an email or sms in which it is claimed that we have a parcel to receive is legitimate, although we weren't expecting any parcel Some people receive fraudulent messages with: "you have a parcel to receive, but... [Read more...]
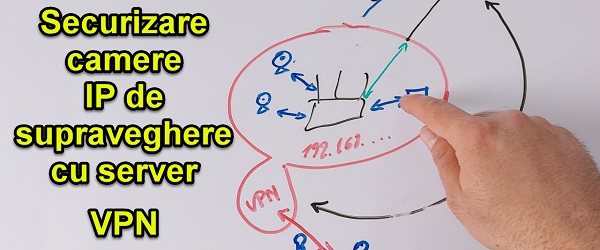
Security of IP cameras with VPN server - STOP port forwarding to cameras
Securing IP Cameras with VPN Server What is the video tutorial about Securing IP Cameras with VPN Server? In the video tutorial Securing IP cameras with VPN server, I will show you how you can secure your surveillance cameras so that no one can access them from the internet. Surveillance cameras are connected to the local network When you connect a [Read more...]
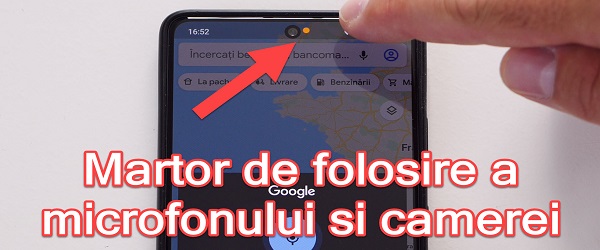
Detector fraudulent use of microphone and camera on Android phones
What is the Fraud Microphone and Camera Use Detector tutorial about? In this video tutorial I present a detector for fraudulent use of microphone and camera, ie an application that detects and notes when the camera and microphone are used on Android phones. Why would we want to know when the camera and microphone on the phone are used… [Read more...]
Simple maximum security setting on Windows - the basis of a protected PC
Setting up simple maximum security on Windows What is the "Setting up maximum security on Windows" tutorial about? In this video tutorial you will see how to set up accounts on Windows so that your operating system is safe. Simple setup of maximum security on Windows. The mistake many Windows users make. At the time of installation… [Read more...]
How not to infect infected sites and viruses - sandboxie
How not to get infected on infected sites and virus applications - sandboxie How not to get infected on infected sites and virus applications - sandboxie In recent years people are increasingly dealing with viruses, spyware and other malicious programs of a new type that have become increasingly sophisticated, and which can be difficult to intercept by a… [Read more...]
How can you find out if someone has been on the computer and what he did
How to find out if someone walked into your computer and what they did Find out who walked your computer and what they did Certainly we all know that we need to put the password on the computer, but most of the time we need to to admit that it is up to us to enter the password every time, so we leave the computer without the password and of course anyone can… [Read more...]
How to find out if your email and password are hackers
How do you know if your email and password are hacked How do you know if your email and password are hacked Nowadays it is more and more difficult to keep our data safe; especially the email address and password, which we use everywhere. When we create an account, we have blind trust Every time you create an account you have to "legitimize" yourself… [Read more...]
How do you stop collecting Windows 10 data - it's like a shredder
How do you stop collecting Windows 10 data, which ended up like a Swiss. Data is collected by any method. Data collection has become a global sport, competing with the largest internet service providers. On the 1st place is Google, followed by Facebook and Microsoft, after which, the ones from Apple, Twitter, Amazon, etc are more shy ... eee, let it recover… [Read more...]









Recent Comments