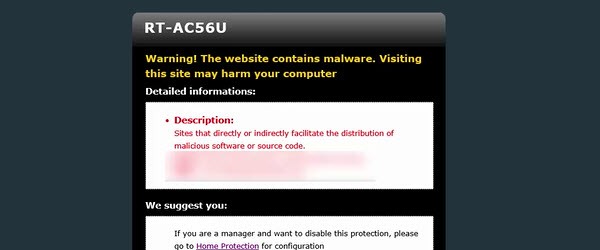
Asus has enriched the routers overnight with a firmware update that offers some extremely useful new features. New features include security and bandwidth management. They are called: 1. AI Protection (TrendMicro security) 2. Adaptive QoS (bandwidth management) If you haven't received the update, you can flash Merlin, a custom firmware for… [Read more...]
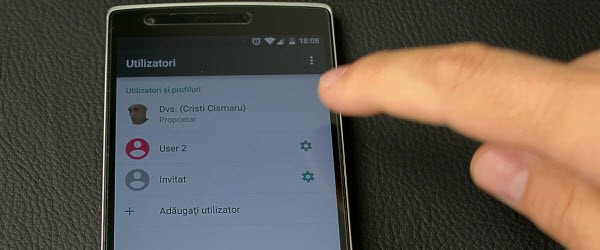
New in Android Lolipop 5, user accounts
Hello friends, today I will present you the most interesting feature introduced with Android 5 Lolipop. It's about the "users" or "user accounts" function. These accounts allow us to keep our data safe, while offering the phone to someone, such as a friend or child. Thus, when we offer someone else's phone, we enter the "Guest" or "Guest" account… [Read more...]
ANTI-HACK, Redirect vulnerability to SMB
Hello friends, today we will solve the problem with the "Redirect to SMB" vulnerability that was discovered a few days ago and that affects all versions of Windows, including Windows 10. The vulnerability is based on the naivety of Windows applications that want to log in as soon as they feel an SMB server. At that moment the login data is spit out, where the attacker… [Read more...]
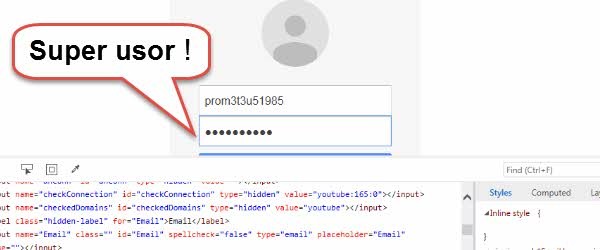
How to find the password in characters dotted browser!
Hello friends! Do you know that moment when when we access a service or a web page, the browser automatically fills in our username and password? Well, as saving as this browser option is to save time and quickly log in to sites visited inside, it is just as dangerous and can leave us accountable if [Read more...]
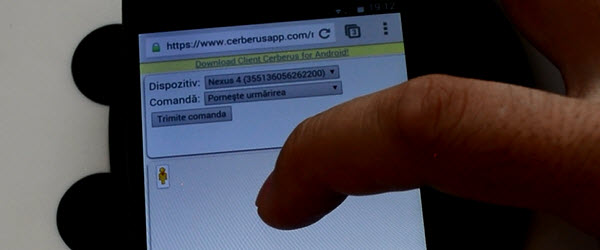
Cerberus, anti-theft application / location resistance reset
Hello friends, in this video tutorial I will introduce you to Cerberus, an android application that offers you superior protection against theft / location / gathering evidence for cases in which your phone is stolen or lost, even in case of total reset of your phone or tablet. Bonus, the Cerberus application can also work as a real keylogger if you want it. ... [Read more...]
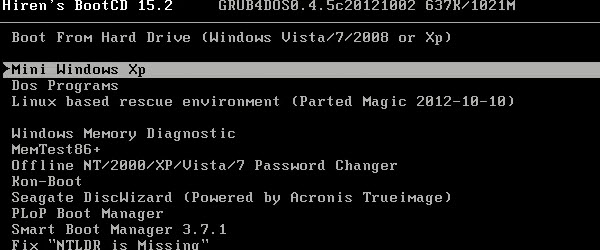
How can we get in Windows 8.1 without password
Hi friends, in today's tutorial we will talk about Windows 8 and Windows 8.1. Specifically, we will see how we can gain access to the operating system if the user account has a password set and we no longer know it. Sometimes we may forget the password of the user account for various reasons. Either because I set it in a hurry, or because I didn't use it anymore… [Read more...]
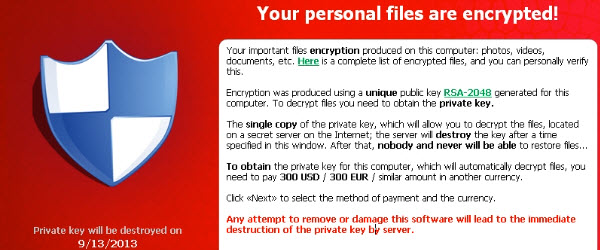
CryptoLocker such as disinfecting prevent and recover files as infected ramsomware
Hi friends, in today's tutorial we will talk about ransomware infection called CryptoLocker. Specifically, we will see how to disinfect a computer infected with CryptoLocker, how to prevent infection with this ransomware and how we can recover files infected with CryptoLocker. What does CryptoLocker do? As I told you above this type of infection is part of the class… [Read more...]








Recent Comments