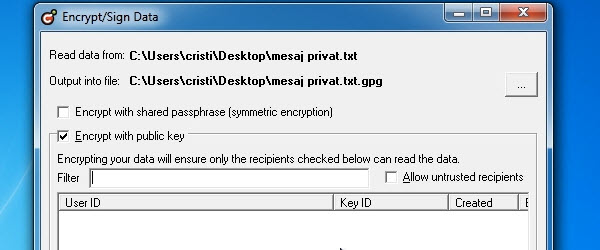
Hi friends, today we will see what can be done for data security and secure exchange of messages. Each of us has private messages to send and receive, these messages must remain private even if someone breaks our facebook account, messenger, gmail , etc. For maximum security we have to encrypt the data, this means that anyone would get their hands on the data… [Read more...]
Simple measures to secure and encrypt traffic navigation
Hi friends, in today's tutorial we will see some tips for safer browsing and encrypted traffic when using a public wireless network. If in yesterday's tutorial about Wireshark, intercepting passwords on free wi-fi networks, my colleague Cristi will show you how easy it is for someone to intercept the data we enter into a site, today [Read more...]
Wireshark, stealing passwords on free wi-fi networks
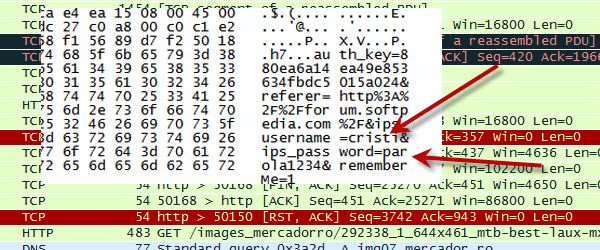
Today we will do something more special, we will try to intercept the login data from the browser with the help of an extraordinary software called Wireshark. I will show you how easy you can lose your password and username if you use them when you are connected on networks. public networks. These networks are the favorite target of attackers, they capture all traffic… [Read more...]
DNS poisoning method commonly used by hackers
DNS poisoning is a method by which hackers give the impression that they have taken control of certain known or unknown sites. DNS is the protocol that makes the link between the domain name and the IP address, because any site in this world has one. or more IP addresses. When we type in the browser "google.com" our computer has three options for finding the address… [Read more...]
How and when we find out if someone has used your computer
Hi friends, in today's tutorial we will see how we can find out when and if someone uses our personal computer. For this we will use a portable application (no installation required) called WinLogOnView that gives us information about the logins that had logged on our computer .WinLogOnView provides us with information about: - Logon ID - Username with… [Read more...]
Zemana AntiLogger or how to protect ourselves against data theft and espionage software - video tutorial
Hello friends, in today's tutorial we will talk about the measures we can take against data theft. The most dangerous infections are Keylogger, software that can record what we type on the keyboard. Keyloggers can range from the simplest, easily traceable to the most complex, very difficult to identify. They can also exist in… [Read more...]
Eliminate ransomware infections with MalwareBytes - video tutorial
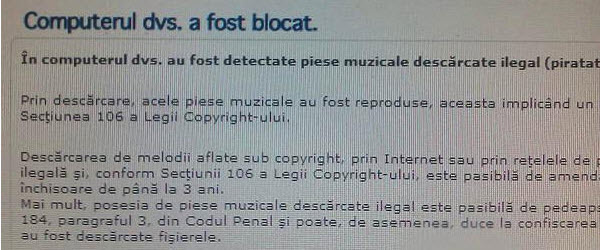
Hi friends, in today's tutorial we will talk about Malwarebytes in the conditions in which we became infected with a ransomware. More recently, a new type of infection is circulating on the Internet, which blocks the user's navigation by redirecting him to a site where a message "Your computer has been blocked" is displayed, informing him that he has illegally downloaded content… [Read more...]






Recent Comments