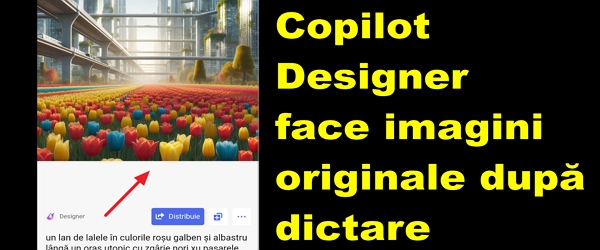
What the video tutorial is about Copilot Designer creates original digital images according to our description In this video tutorial under the title Copilot Designer creates original digital images according to our description, I introduce the Designer function in Microsoft Copilot, which is responsible for creating images based on the user's description with the help of intelligence... [Read more...]
Copilot Designer creates original digital images according to our description
Easy to clean air conditioner recommendation – Midea All Easy Pro Nordic
Easy to clean air conditioner recommendation What is this video about with the title Easy to clean air conditioner recommendation? This article ( Easy to clean air conditioner recommendation ) is actually a recommendation for anyone who wants to buy an air conditioner. A very serious problem that must be taken into account with air appliances... [Read more...]
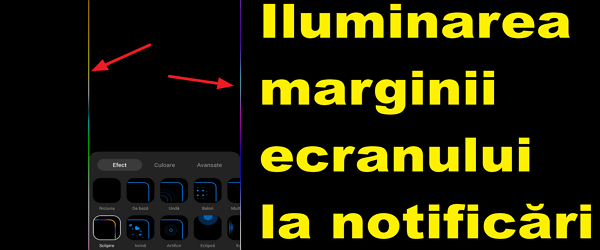
Edge screen lighting for notifications – more discreet notifications
What is it about in the tutorial Lighting the screen on the edge for notifications? In this video tutorial (Lighting the screen on the edge during notifications) I will show you how you can have edge lighting or the lighting of the screen on the edge when there are notifications. This function is found natively on some phones (Samsung, Xiaomi, etc.), but it can also be obtained through... [Read more...]
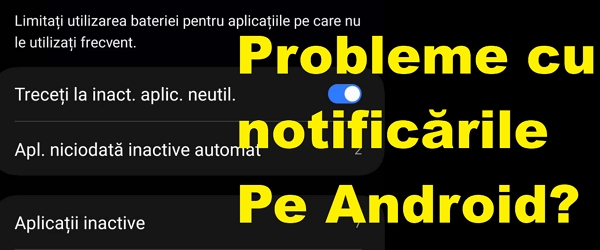
Fix notification issues on Android – it can be from your phone
What's in the tutorial Solving problems with notifications on Android In today's tutorial (Solving problems with notifications on Android) we will see what are the causes that can lead to the interruption of notifications from certain applications on Android Problems with notifications can come from two parts Problems with the server side of … [Read more...]
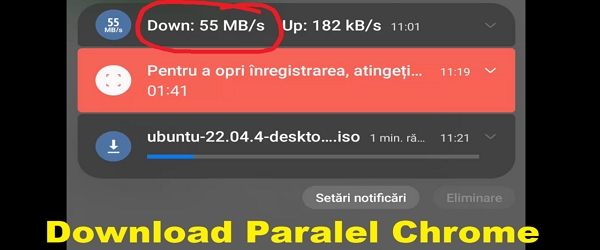
Increase download speed in Google Chrome with parallel downloads
What is the video tutorial Increase download speed in Google Chrome about? In this video tutorial, Increasing download speed in Google Chrome, I present a function from Google Chrome Flags, which helps to download the same file from several places in parallel. Thus the download speed increases. Similar to the BitTorrent protocol This setting that Google … [Read more...]
How to make Whatsapp conversations invisible - nothing is visible
What the tutorial How to make invisible conversations on Whatsapp is about In this tutorial under the title How to make invisible conversations on Whatsapp, I present to you the best method to hide conversations with contacts or in Whatsapp groups. Many don't know about this method of hiding Whatsapp conversations Many only know about blocking … [Read more...]
2024 New Features in Google Maps – Immersive Routes and Time Travel
2024 New Features in Google Maps What is the 2024 New Features in Google Maps tutorial about? In today's video tutorial ( New functions 2024 in Google Maps ) I will present you some new functions, introduced by Google in Maps Trasee or immersive routes assisted by AI When you want to go from one place to another, Google Maps makes the route for you the most suitable and you ... [Read more...]
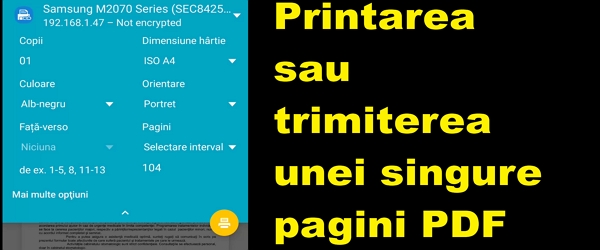
Print or send a single PDF page – no apps
What the video tutorial Print or send a single page PDF is about In this video tutorial entitled Print or send a single page PDF we will see how to send or print a single page from a longer PDF document without to use other applications. Stop taking pictures on digital pages! When you want to… [Read more...]
Samsung phone health check app – official app
Samsung phone health check application What is the Samsung phone health check application tutorial about? In this video tutorial "Application for checking the health of Samsung phones" I present to you an application from Samsung, in which we have a very useful function for diagnosing phones... [Read more...]
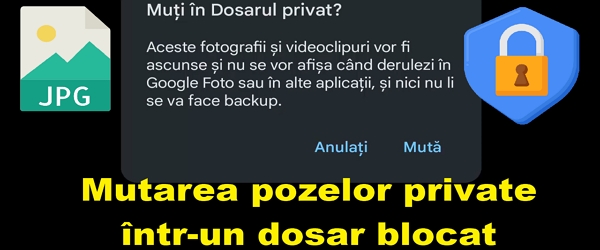
Hide private pictures in a locked folder – separate from the gallery
Hide private pictures in a locked folder What is the tutorial Hide private pictures in a locked folder about? In this video tutorial titled Hide private pictures in a locked folder , I show you a method by which you can move private pictures from the gallery to a locked folder that you can only open with your fingerprint This method of … [Read more...]










Recent Comments