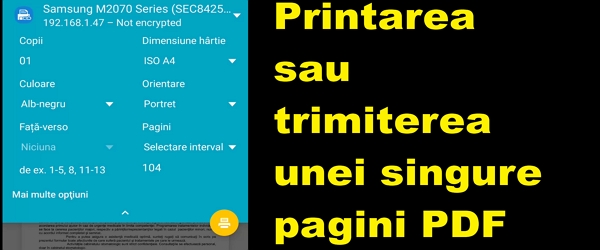
What the video tutorial Print or send a single page PDF is about In this video tutorial entitled Print or send a single page PDF we will see how to send or print a single page from a longer PDF document without to use other applications. Stop taking pictures on digital pages! When you want to… [Read more...]
My Wallet Emag cashless shopping – also goes on Fashion Days
My Wallet Emag shopping without money What is the My Wallet Emag shopping without money tutorial about? In this video tutorial My Wallet Emag shopping without money , I introduce you to My Wallet. This is a new feature from Emag and Fashion Days that will allow you to buy products even if you don't have money in your account What are My Wallets from Emag or... [Read more...]
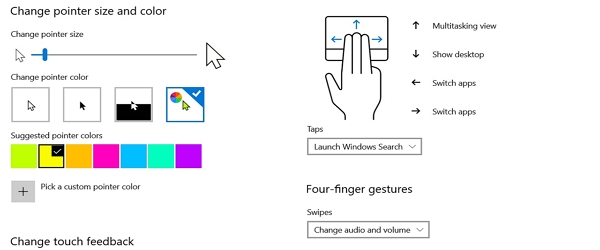
Customize Windows touchpad and mouse settings – make them your way
What the Customize Windows Touchpad and Mouse Settings video tutorial is about In today's video tutorial, called Customize Windows Touchpad and Mouse Settings, I show you the settings you can use to customize your mouse and touchpad. We're going to change the way both the mouse cursor, mouse behavior, and touchpad behavior, for a… [Read more...]
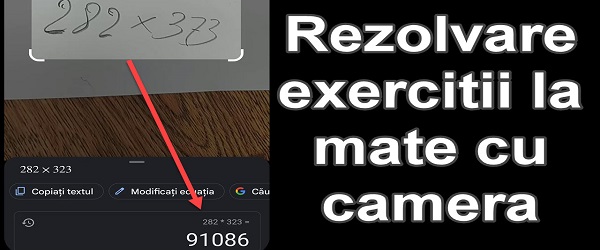
Solving calculations visually with Google Lens - solving math exercises quickly
What is the video tutorial Solving calculations visually with Google Lens about? In the video tutorial Solving calculations visually with Google Lens, I present one of the functions that Google Lens makes available to us, namely solving mathematical calculations visually. What does it mean to solve mathematical calculations visually? Let's say we have an exercise written on paper... [Read more...]
QR Code with direct dialing – instead of a phone number on the windshield, in the parking lot
QR Code with Dialer What is the QR Code with Direct Dialer tutorial about? I'm going to show you how to make a QR Code with direct dialing for when we park in different areas, so we don't get confused. We will extremely quickly make a QR code to put in the windshield, so that we can be called faster. What is a QR Code? The QR Code is a code that hides behind it... [Read more...]
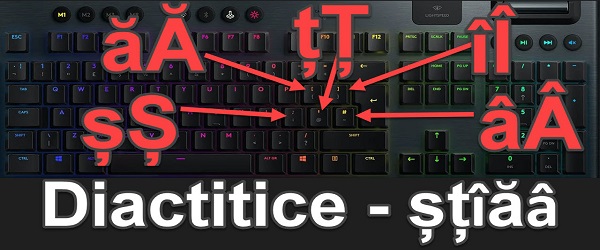
Writing with diacritics on international keyboards – â – ă – ȣȚ – îÎ – șȘ
What is the tutorial Writing with diacritics on international keyboards about? In the video tutorial Writing with diacritics on international keyboards, I show you a better way to write with diacritics on international keyboards, such as QWERTY US, QWERTY UK, etc. It is a software method that is activated from Windows and does not require the installation of any software... [Read more...]
How to translate a PDF document - free document translation
What is the tutorial on how to translate a PDF document about? In this video tutorial you will see how to translate a PDF document. It is the simplest and fastest way to translate a PDF document. How to translate an entire PDF document? You must have the document already downloaded on your PC or phone. In your browser, go to Google Translate (on ... [Read more...]
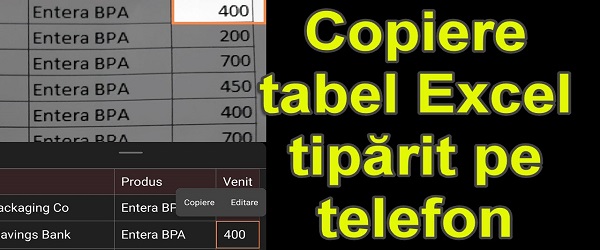
Importing printed Excel tables into the phone - OCR goes to the tables
Importing Printed Excel Tables into Your Phone What is the Video Tutorial for Importing Printed Excel Tables into Your Phone? In these video tutorials "Importing Excel spreadsheets into your phone", I show you how you can import Excel spreadsheets onto paper into your Office. Import printed Excel tables into the Office application Whatever you want to [Read more...]
Copy text from pictures to phone - copy paste text from pictures
What is the Copy Text from Images on Phone tutorial about? In the video tutorial Copying text from images to your phone, I'll show you how to copy text from images. I mean text that can't be copied because it's part of the image. This procedure is useful when we want to copy text from images on the net, [Read more...]
Phone printing application via USB - without PC - USB only
What is the USB print application tutorial about? In the video printing application tutorial on the phone via USB, I will show you how you can print documents to the printer without a PC, only with your phone. You'll see how to connect your phone to the printer with a USB OTG cable and a free Play Store app. Why should I … [Read more...]











Recent Comments