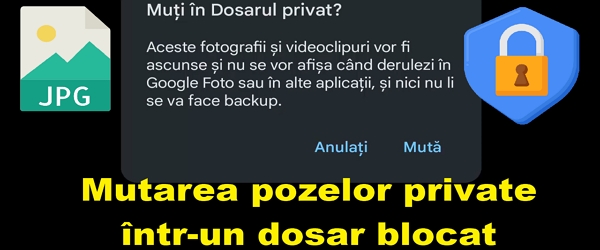
Hide private pictures in a locked folder What is the tutorial Hide private pictures in a locked folder about? In this video tutorial titled Hide private pictures in a locked folder , I show you a method by which you can move private pictures from the gallery to a locked folder that you can only open with your fingerprint This method of … [Read more...]
Hide private pictures in a locked folder – separate from the gallery
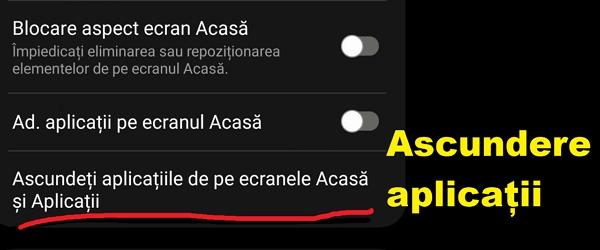
Hiding installed apps on Samsung phones
What is the video tutorial Hide installed apps on Samsung phones about? In this video tutorial "Hiding installed applications on Samsung phones" I will show you how to hide installed applications on Samsung phones, without using a third-party launcher Why hide installed applications? The answer is obvious and the reasons are… [Read more...]
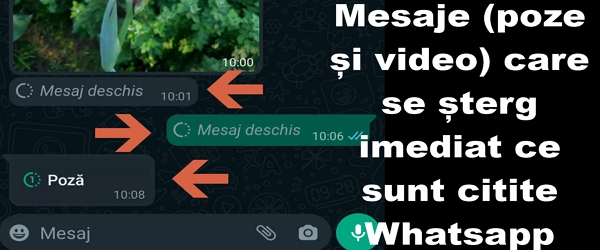
Whatsapp single view video pictures that delete as soon as they are seen
Whatsapp single view video pictures What is the video tutorial about Whatsapp single view video pictures In this video tutorial "Whatsapp single view video pictures" I introduce you the feature in Whatsapp which is called single view. What does Single View feature in Whatsapp do? The basic idea with the single display feature is to send a picture or video, and… [Read more...]
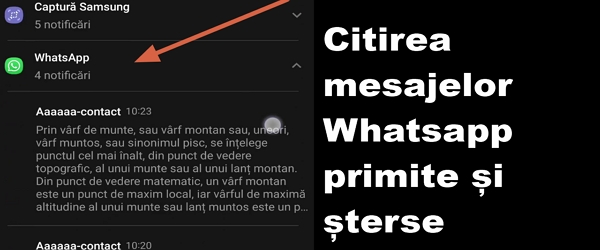
How to view received and deleted messages in Whatsapp
What is the video tutorial about How to view received and deleted messages from Whatsapp In this tutorial I present you a simple way through which you can view received and deleted messages from Whatsapp. How do we do this? Simple, through the notification history. How to view received and deleted Whatsapp messages Received and deleted Whatsapp messages can no longer … [Read more...]
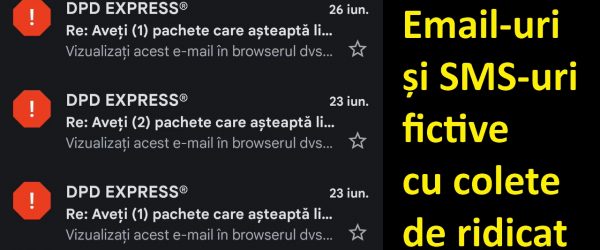
Fraudulent messages with unaddressed parcels – how we tell
What is the video tutorial Fraudulent messages with unaddressed parcels about In this video tutorial Fraudulent messages with unaddressed parcels we will see how we can tell if an email or sms in which it is claimed that we have a parcel to receive is legitimate, although we weren't expecting any parcel Some people receive fraudulent messages with: "you have a parcel to receive, but... [Read more...]
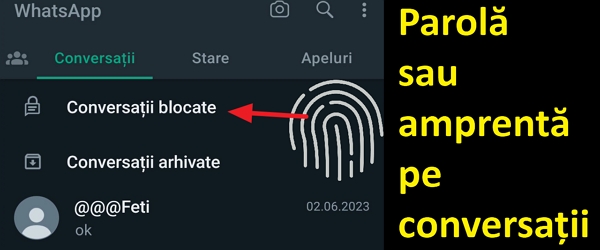
Hide and password chat on Whatsapp – password or fingerprint
What is the video tutorial Hiding and passwording a conversation on Whatsapp about In the video tutorial Hiding and passwording a conversation on Whatsapp I will show you how to hide and how to protect with a fingerprint or password a conversation on Whatsapp Why hide a conversation on Whatsapp? Why do we have curtains, drapes, fences, bathroom door :-) and other things... [Read more...]
Mikrotik hAP ax3 router review excellent – very good speed on USB
What is this video review about: Mikrotik hAP ax3 review great router? Mikrotik hAP ax3 excellent router review - In this review I present a WiFi 6 router from Mikrotik model hAP ax3. It's part of the AX1800 class but comes with some top specs and some blistering USB speeds. What is Mikrotik? Mikrotik is a European company... [Read more...]
How to achieve 2400 Mbps on Wi-Fi - and how to set your router to 160Mhz
What is it about in the tutorial How to reach 2400 Mbps on Wi-Fi In the video tutorial How to reach 2400 Mbps on Wi-Fi we will see how to achieve the speed of 2400 Mbps when using a Wi-Fi 6 AX 3000 router from any manufacturer, but which supports the channel width of 160 Mhz. What is a Wi-Fi channel? A WiFi channel is a specific frequency range used by… [Read more...]
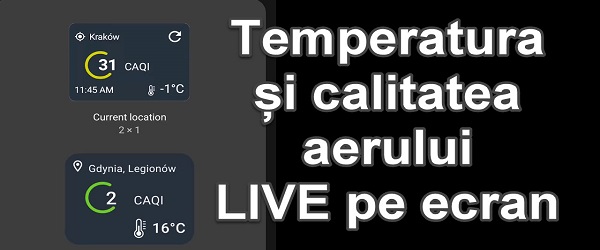
Temperature and Air Quality Widget – REAL LIVE POLLUTION
What is the temperature and air quality Widget video tutorial about? In this video tutorial "Temperature and air quality widget", I present you the most handy method to find out what the exact temperature is outside and what the live air quality is. How can we have a live air temperature and air quality widget? Airly is a… [Read more...]
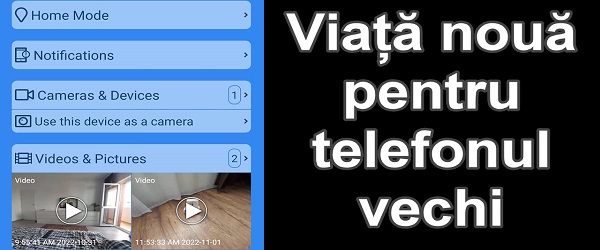
Presence turns your phone into an IP camera – don't throw away your old phone!
Presence makes an IP camera from the phone What is the video tutorial Presence makes an IP camera from the phone about? In this video tutorial, I present Presence, an application that turns your phone into an IP camera. In practice, I will show you how you can make a surveillance system using only one or more phones. What does the Presence app do? Presence is a… [Read more...]









Recent Comments