How to block abusive BITCOIN mining on PC What about abusive BITCOIN MINING? Lately, due to the ever-increasing price of BITCOIN, hackers are looking for more and more interesting methods of mining BITCOIN. The last method consists in using the processing power of several computers, through software or web scripts, which transform… [Read more...]
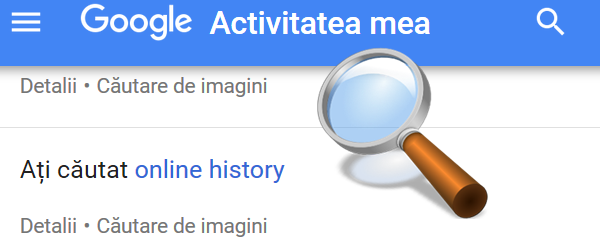
How do I delete my local and online web history - the history on Google servers
How do I delete my local and online WEB history? Browsing history - what is it? Browsing history or history is the amount of data that our browser retains when visiting websites. For example: If we go to emag.ro, the browser will store the following data locally (on phone, laptop, pc, tablet): 1. Page visited (web address) 2. Time and date of visit… [Read more...]
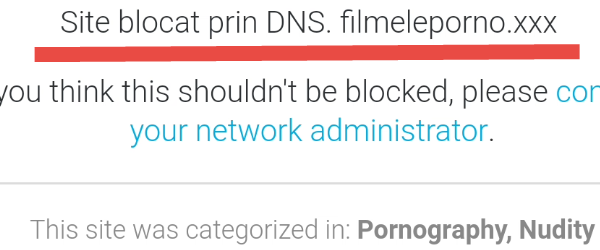
Blocking children from accessing ADULT websites
Blocking children's access to Adult sites I do not want to morale on this site, which is quite technical, but I must say that a child is good to live his childhood. The duty of parents or older siblings! From my point of view, any responsible adult should be careful where his child goes on the internet, and if he can't or if he doesn't [Read more...]
Fixing the screen in an application on Android - the antidote for curious
Fixing the screen in an Android application is a function that allows us to fix our screen, to stay in a single application and not be able to exit until we enter a password or fingerprint. On which phones can you fix the screen? This feature should be available on any phone with android 5.0 or higher. Now it also depends on the developer, if he decided to… [Read more...]
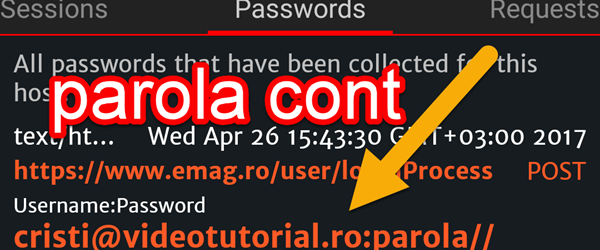
As you can see passwords, pictures and pages to others - affected online stores
How do you see the passwords, pictures and pages of others - online stores affected Security IT security is quite vague nowadays, when the average user does not differentiate between web vulnerability and virus. We tried to inform as much as possible, but unfortunately the message does not seem to get where it should. On the contrary, we see that online stores very foarte [Read more...]
Parental control android tablets and phones for children
Android parental control, a sum of measures that any parent, who gives the child access to PC / tablet / laptop or phone, should institute, first of all. Parental control blocks children's access to dangerous video content (porn, gambling, violence, etc.). Unfortunately, many parents have no idea how to operate a tablet or a phone and from here… [Read more...]
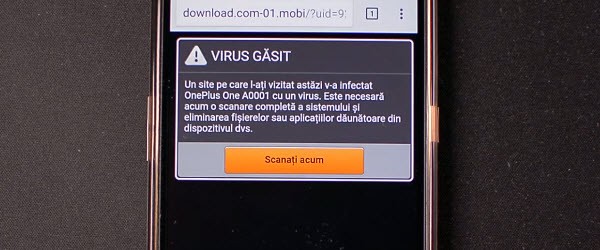
How to get rid of scareware phone
Scareware programs or pages are a special and very passive category of malware. They are a kind of phishing that is based on users' fears to determine them to perform certain actions. A scareware can urge you to install software, disclose personal data, pay a certain amount of money or send an SMS to a number with [Read more...]
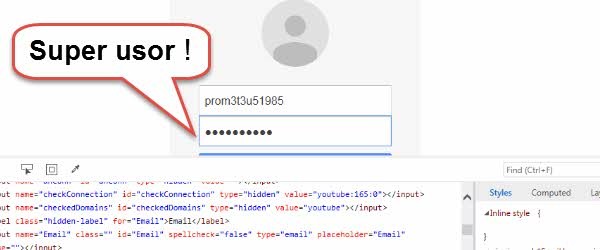
How to find the password in characters dotted browser!
Hello friends! Do you know that moment when when we access a service or a web page, the browser automatically fills in our username and password? Well, as saving as this browser option is to save time and quickly log in to sites visited inside, it is just as dangerous and can leave us accountable if [Read more...]
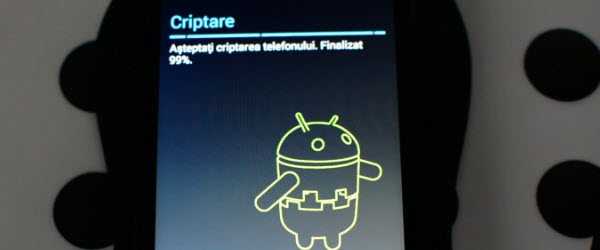
Encryption android phone or tablet before sale
Hi friends, I know that maybe the title may seem strange but I promise it is very correct. Before selling a phone or tablet, they need a more careful cleaning treatment, here I do not mean the physical cleaning but the cleaning of the internal memory, so that the data can no longer be recovered. Data can be recovered from any phone, even if [Read more...]










Recent Comments