Different IP cameras in one application Each surveillance camera manufacturer has its own application with which you can watch live images transmitted by that camera or those surveillance cameras. Problems arise when we have surveillance cameras from different manufacturers. Then you need to open an application for each room. Rooms [Read more...]
How not to infect infected sites and viruses - sandboxie
How not to get infected on infected sites and virus applications - sandboxie How not to get infected on infected sites and virus applications - sandboxie In recent years people are increasingly dealing with viruses, spyware and other malicious programs of a new type that have become increasingly sophisticated, and which can be difficult to intercept by a… [Read more...]
USB stick password - portable safety
USB stick password USB stick password - portable security The need to keep your data safe is becoming more and more important, especially in the context of data leaks, unlimited data collection or computer attacks of any kind. Our data is almost 100% in digital format People are starting to realize (a bit late) that the data they… [Read more...]
How can you find out if someone has been on the computer and what he did
How to find out if someone walked into your computer and what they did Find out who walked your computer and what they did Certainly we all know that we need to put the password on the computer, but most of the time we need to to admit that it is up to us to enter the password every time, so we leave the computer without the password and of course anyone can… [Read more...]
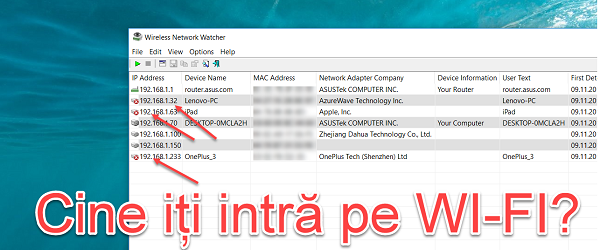
Who connects illegally on your WI-FI network
Who connects illegally on your WI-FI network The wireless signal passes through the walls of the house. When we use a Wi-Fi network in our home, we need to be aware that that wireless network can also be accessed by other people, neighbors, or people nearby. Better security of the Wi-Fi network We have spoken on other occasions about security when logging in… [Read more...]
How to find out if your email and password are hackers
How do you know if your email and password are hacked How do you know if your email and password are hacked Nowadays it is more and more difficult to keep our data safe; especially the email address and password, which we use everywhere. When we create an account, we have blind trust Every time you create an account you have to "legitimize" yourself… [Read more...]
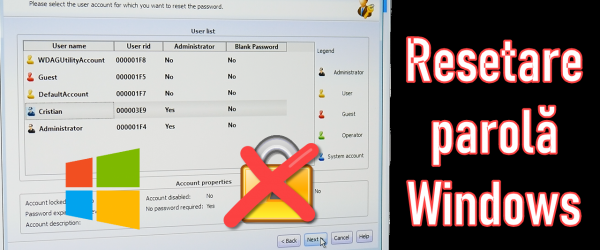
How to reset your Windows password if you forget it :-)
How to reset your Windows password if you forgot it How to reset your Windows password if you forgot it? In case you forgot your Windows password, you have two options. The first is to reset the password and the second is to reinstall Windows. On which Windows operating systems does password reset work? Windows password reset, ie the method presented in this [Read more...]
YouTube Kids a special YouTube app for kids
YouTube Kids a special YouTube app for kids Kids sit on their tablet or phone, BUT! The digital world and technology are good when used constructively, but they can also be bad when not used properly. For example, when children enter YouTube, they can find very useful information, but also certain videos that can "attract their attention"… [Read more...]
How do you stop collecting Windows 10 data - it's like a shredder
How do you stop collecting Windows 10 data, which ended up like a Swiss. Data is collected by any method. Data collection has become a global sport, competing with the largest internet service providers. On the 1st place is Google, followed by Facebook and Microsoft, after which, the ones from Apple, Twitter, Amazon, etc are more shy ... eee, let it recover… [Read more...]











Recent Comments