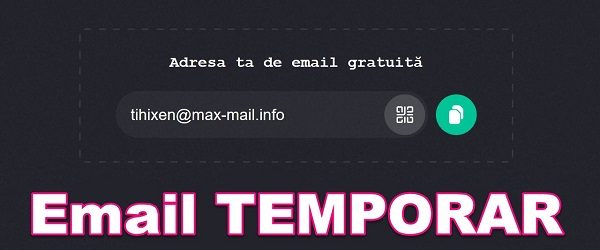
Temporary email, the permanent email saver Anyone who uses an email address knows that at some point, after some time of use, the email box is filled with spam (unsolicited email) with all kinds of offers or who knows what products. We end up in this situation because over time we used our email address too lightly and left it all [Read more...]
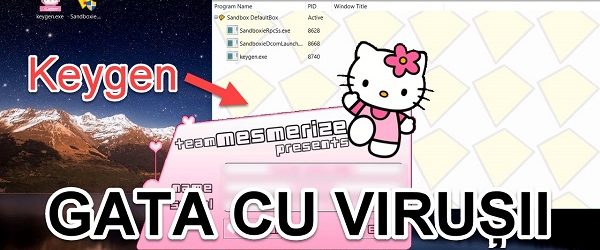
How not to infect infected sites and viruses - sandboxie
How not to get infected on infected sites and virus applications - sandboxie How not to get infected on infected sites and virus applications - sandboxie In recent years people are increasingly dealing with viruses, spyware and other malicious programs of a new type that have become increasingly sophisticated, and which can be difficult to intercept by a… [Read more...]
USB stick password - portable safety
USB stick password USB stick password - portable security The need to keep your data safe is becoming more and more important, especially in the context of data leaks, unlimited data collection or computer attacks of any kind. Our data is almost 100% in digital format People are starting to realize (a bit late) that the data they… [Read more...]
How can you find out if someone has been on the computer and what he did
How to find out if someone walked into your computer and what they did Find out who walked your computer and what they did Certainly we all know that we need to put the password on the computer, but most of the time we need to to admit that it is up to us to enter the password every time, so we leave the computer without the password and of course anyone can… [Read more...]
How to find out if your email and password are hackers
How do you know if your email and password are hacked How do you know if your email and password are hacked Nowadays it is more and more difficult to keep our data safe; especially the email address and password, which we use everywhere. When we create an account, we have blind trust Every time you create an account you have to "legitimize" yourself… [Read more...]
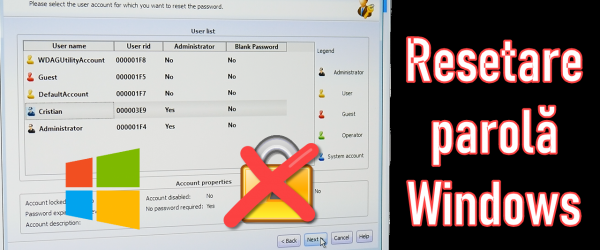
How to reset your Windows password if you forget it :-)
How to reset your Windows password if you forgot it How to reset your Windows password if you forgot it? In case you forgot your Windows password, you have two options. The first is to reset the password and the second is to reinstall Windows. On which Windows operating systems does password reset work? Windows password reset, ie the method presented in this [Read more...]
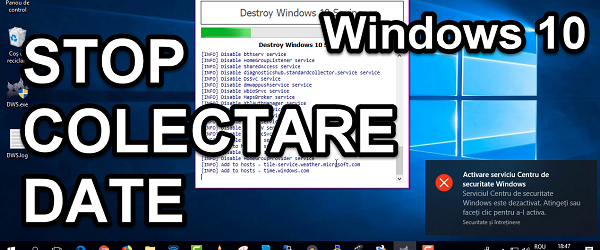
How do you stop collecting Windows 10 data - it's like a shredder
How do you stop collecting Windows 10 data, which ended up like a Swiss. Data is collected by any method. Data collection has become a global sport, competing with the largest internet service providers. On the 1st place is Google, followed by Facebook and Microsoft, after which, the ones from Apple, Twitter, Amazon, etc are more shy ... eee, let it recover… [Read more...]
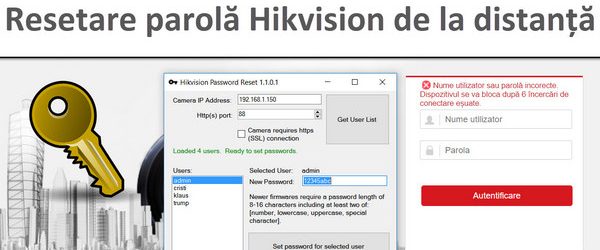
Reset IP Remote Hikvision IP Camera Password (CAUTION)
Resetting the Hikvision IP camera password remotely (dangerous). the last tool presented in the tutorial is really evil. EVEN IF YOU WANT TO RESET OR NOT THE PASSWORD ON THE CAMERA, IT WOULD BE GOOD TO WATCH THE TUTORIAL. Surveillance cameras are those devices that you install once, then forget about them. But sometimes we need to go to them and then BUM, I forgot my password. ... [Read more...]
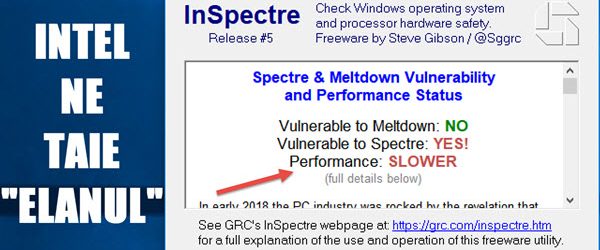
WEAKER PCS OVERNIGHT - SOLUTION update Meltdown
Why are PCs weaker overnight - SOLVING meltdown update How are Meltdown, Specter and PC performance? A few days ago I told you about the Meltdown and Specter vulnerabilities, as a result of which Windows and Linux updates were released. System updates can only resolve the Meltdown vulnerability, with manufacturers… [Read more...]
How to block the misuse of BITCOIN on your PC
How to block abusive BITCOIN mining on PC What about abusive BITCOIN MINING? Lately, due to the ever-increasing price of BITCOIN, hackers are looking for more and more interesting methods of mining BITCOIN. The last method consists in using the processing power of several computers, through software or web scripts, which transform… [Read more...]










Recent Comments